How to connect to AWS via Site-to-Site VPN using Juniper SRX300
Contributed by: Takeshi Miyaoka on Saturday, July 27 2024
Last modified on Saturday, August 24 2024
I would like to describe how to establish a Site-to-Site VPN connection with AWS using SRX300.
Create an environment with the configuration shown in the image below.
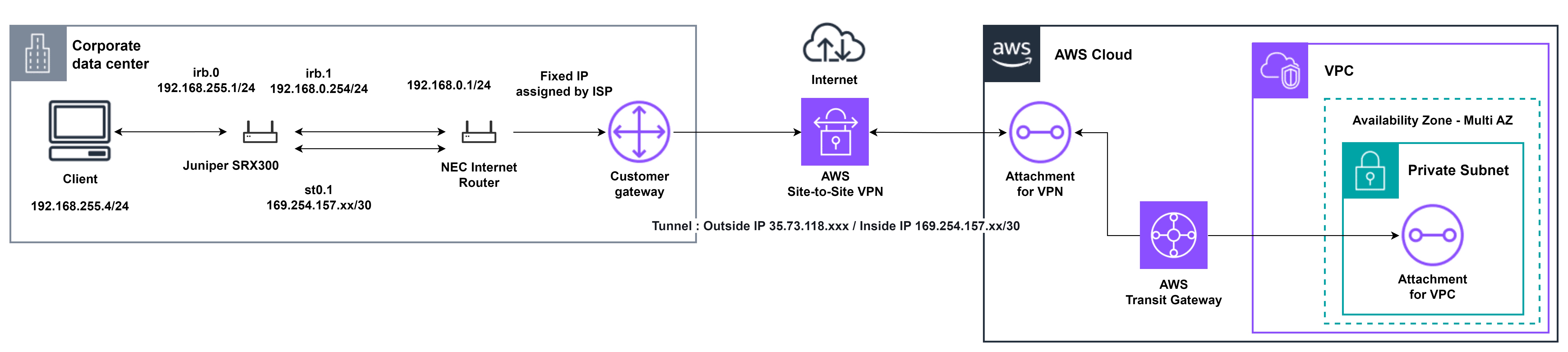
The tasks to be performed are as follows:
(1) Work on the AWS side
- Create a customer gateway
- Create a transit gateway
- Create a Site-To-Site VPN connections
- Create a transit gateway attachment
(2) Work on the SRX300 side
- Interface configuration
- Configuring VLANs
- Configuring protocols
- Setting policy-options
- Security Settings
(1) Work on the AWS side
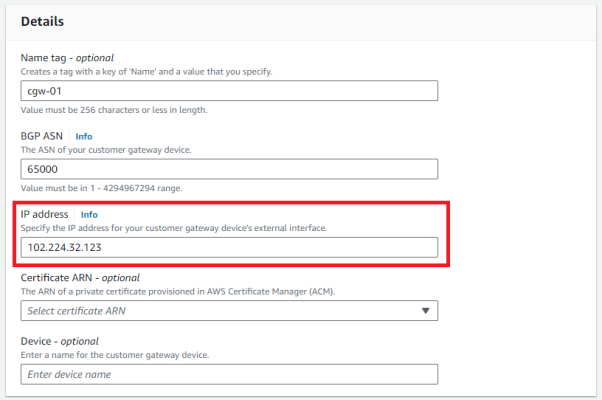
1.Create a customer gateway
From the VPC menu, select Customer gateways.
Set the on-premises global IP address to the IP address.
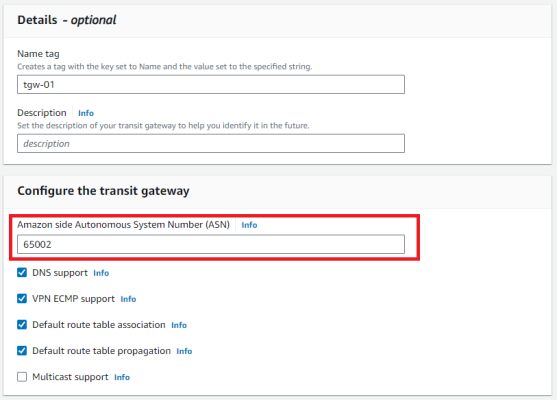
2.Create a transit gateway
From the VPC menu, select Trasnit gateways.
Set an unused ASN on both the on-premises network and the AWS network to avoid duplication of the same number.
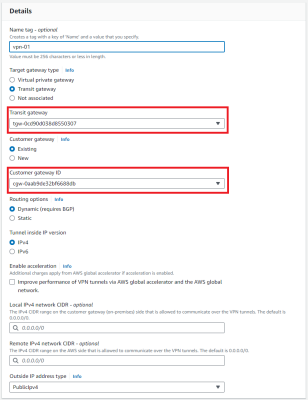
3.Create a Site-To-Site VPN Connections
From the VPC menu, select Site-to-Site VPN connections
Configure the customer gateway and transit gateway that you created in the previous step.
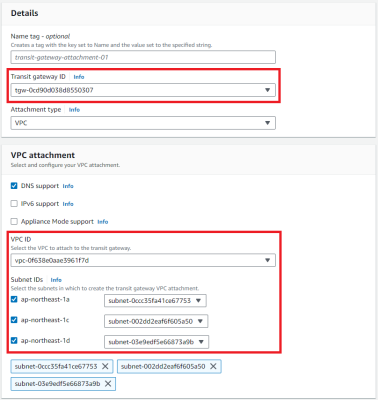
4.Create a Site-To-Site VPN Connections
Finally, create a transit gateway attachment. The menu is in the same place as the transit gateway.
Configure the transit gateway you created in the previous step and the VPC to which it will be connected.
(2) Work on the SRX300 side
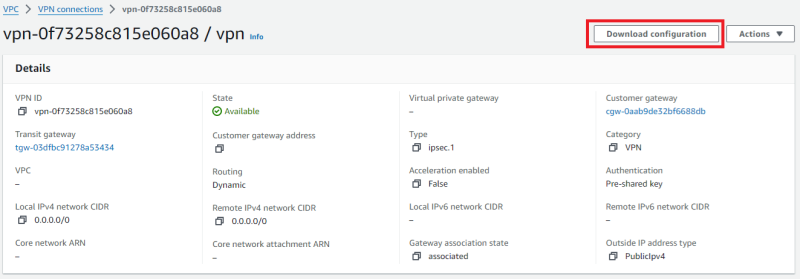
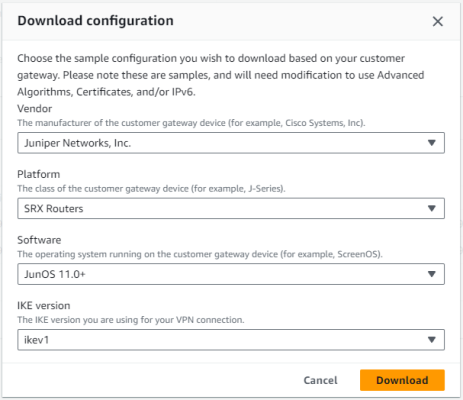
First, download the configuration that is automatically generated on the AWS side from Site-to-Site- VPN connections to set up the SRX300. It may not be usable as is, so you will need to modify it to suit your environment.
When you press the download button, the following pop-up will appear, so select Juniper SRX.
The configuration will be completed by executing the commands in the downloaded configuration in order, but some commands may not be usable as is, so please refer to the configuration information below.
1.Interface configuration
Check the interface definitions on the SRX side that will connect to AWS via VPN.
interfaces {
interface-range interface-untrust {
member-range ge-0/0/0 to ge-0/0/1;
unit 0 {
family ethernet-switching {
vlan {
members vlan-untrust;
}
}
}
}
interface-range interface-trust {
member-range ge-0/0/2 to ge-0/0/5;
unit 0 {
family ethernet-switching {
vlan {
members vlan-trust;
}
}
}
}
irb {
unit 0 {
family inet {
address 192.168.255.1/24;
}
}
unit 1 {
family inet {
address 192.168.0.254/24;
}
}
}
st0 {
unit 1 {
family inet {
mtu 1436;
address 169.254.157.xx/30; # You will find your value in the downloaded config.
}
}
}
}2.Configuring VLANs
This is the minimum definition required to create the network configuration shown in the diagram at the beginning.
vlans {
vlan-trust {
vlan-id 3;
l3-interface irb.0;
}
vlan-untrust {
vlan-id 4;
l3-interface irb.1;
}
}3.Configuring protocols
protocols {
bgp {
group ebgp {
type external;
neighbor 169.254.157.xx { # You will find your value in the config.
hold-time 30;
export EXPORT-DEFAULT;
peer-as 65xxx; # You will find your value in the downloaded config.
local-as 65xxx; # You will find your value in the downloaded config.
}
}
}
l2-learning {
global-mode switching;
}
}4.Setting policy-options
policy-options {
policy-statement EXPORT-DEFAULT {
term default {
from {
route-filter 0.0.0.0/0 exact;
}
then accept;
}
term reject {
then reject;
}
}
}5.Security Settings
Particular care must be taken to ensure that the policies and zones settings are correct.
Configure IKE
security {
ike {
proposal ike-prop-vpn-1 {
authentication-method pre-shared-keys;
dh-group group2;
authentication-algorithm sha1;
encryption-algorithm aes-128-cbc;
lifetime-seconds 28800;
}
policy ike-pol-vpn-1 {
mode main;
proposals ike-prop-vpn-1;
pre-shared-key ascii-text "# You will find your value in the downloaded config.";
}
gateway gw-vpn-1 {
ike-policy ike-pol-vpn-1;
address 35.73.118.xxx; # You will find your value in the downloaded config.
dead-peer-detection;
no-nat-traversal;
external-interface irb.1;
}
}Configure ipsec
security {
ipsec {
proposal ipsec-prop-vpn-1 {
protocol esp;
authentication-algorithm hmac-sha1-96;
encryption-algorithm aes-128-cbc;
lifetime-seconds 3600;
}
policy ipsec-pol-vpn-1 {
perfect-forward-secrecy {
keys group2;
}
proposals ipsec-prop-vpn-1;
}
vpn vpn-1 {
bind-interface st0.1;
df-bit clear;
ike {
gateway gw-vpn-1;
ipsec-policy ipsec-pol-vpn-1;
}
}
}
}Configure flow
security {
flow {
tcp-mss {
ipsec-vpn {
mss 1379;
}
}
}
}Configure policies
security {
policies {
from-zone trust to-zone untrust {
policy All_trust_untrust {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone trust to-zone VPN {
policy VPN-OUT {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
from-zone VPN to-zone trust {
policy VPN-IN {
match {
source-address any;
destination-address any;
application any;
}
then {
permit;
}
}
}
}
}Configure zones
security {
zones {
security-zone trust {
host-inbound-traffic {
system-services {
all;
}
protocols {
all;
}
}
interfaces {
irb.0;
}
}
security-zone VPN {
host-inbound-traffic {
system-services {
ping;
}
}
interfaces {
st0.1;
}
}
security-zone untrust {
host-inbound-traffic {
system-services {
ike;
ping;
}
}
interfaces {
irb.1;
}
}
}
}appendix
The ipsec status of SRX can be checked with the following command.
ike
Verify that the status is up.
[edit]
root@srx300# run show security ike security-associations
Index State Initiator cookie Responder cookie Mode Remote Address
6684709 UP d34a272d9d4dd54c f07aeb3a6a029d0e Main 35.73.118.xxxipsec
Verify that the number of total active tunnels is greater than or equal to 1.
[edit]
root@srx300# run show security ipsec security-associations
Total active tunnels: 1
ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway
<131073 ESP:aes-cbc-128/sha1 8d5c0429 839/ unlim - root 500 35.73.118.xxx
>131073 ESP:aes-cbc-128/sha1 ce95db49 839/ unlim - root 500 35.73.118.xxxstatistics
You can view statistics on encryption and decryption.
[edit]
root@srx300# run show security ipsec statistics
ESP Statistics:
Encrypted bytes: 73849152
Decrypted bytes: 25305315
Encrypted packets: 301138
Decrypted packets: 291708
AH Statistics:
Input bytes: 0
Output bytes: 0
Input packets: 0
Output packets: 0
Errors:
AH authentication failures: 0, Replay errors: 0
ESP authentication failures: 0, ESP decryption failures: 0
Bad headers: 0, Bad trailers: 0